
Advantages of using a SaaS cloud monitoring system
September 12, 2019
Server monitoring with iLO (HP), iDRAC (DELL) and IPMI technologies with Zabbix
January 12, 2020

Monitor your Windows servers and discover what nobody sees
Microsoft Windows Server is one of the most popular types of servers worldwide and can be used to cover a wide range of functionalities for our companies. From web or mail server, to application server or domain controller. In this article we are going to talk about the monitoring of this type of servers and we will emphasize the events that we can observe with its viewer.
Like any other type of server, the applications that run on them are often of vital importance to your business. So, a fall can impact very dangerously. If we have a development environment in running on it, all our team of programmers would be disabled to work until the problem was solved. If it were our mail server, the whole company would be temporarily cut off by this way. For all this, it is very important to know what is happening in our Microsoft Windows Server.
Windows allows us access to a large number of metrics. So, it is necessary to know well what is going to run inside our server and what we are going to use it for, since, depending on this, there will be metrics that will be more important than others.
It is always of great interest to have the resources at your disposal under control, to see how your consumption evolves. Resources such as CPU, Memory, disk or traffic are essential to know the functioning of the server and its work peaks. The percentage of time that the processor is working, pending processes, available memory, etc. are some of the parameters that can warn us of an anomalous operation.
Like any other type of server, the applications that run on them are often of vital importance to your business. So, a fall can impact very dangerously. If we have a development environment in running on it, all our team of programmers would be disabled to work until the problem was solved. If it were our mail server, the whole company would be temporarily cut off by this way. For all this, it is very important to know what is happening in our Microsoft Windows Server.
Windows allows us access to a large number of metrics. So, it is necessary to know well what is going to run inside our server and what we are going to use it for, since, depending on this, there will be metrics that will be more important than others.
It is always of great interest to have the resources at your disposal under control, to see how your consumption evolves. Resources such as CPU, Memory, disk or traffic are essential to know the functioning of the server and its work peaks. The percentage of time that the processor is working, pending processes, available memory, etc. are some of the parameters that can warn us of an anomalous operation.

Beyond these numerical records, how can we know what application has been started and is consuming our resources? How can we know who has started that application? How can we know that a BLUE SCREEN has appeared?
Every operation performed in Windows is recorded in its event log, from the beginning of a user session, to an application. The event viewer allows us to have a more legible view of what is happening. In addition, all the problems in our system that leads to an increase in the consumption of its resources will coincide in time with the events that appear in the viewer. This will allow us to trace them and find the origin of the failure.
Every operation performed in Windows is recorded in its event log, from the beginning of a user session, to an application. The event viewer allows us to have a more legible view of what is happening. In addition, all the problems in our system that leads to an increase in the consumption of its resources will coincide in time with the events that appear in the viewer. This will allow us to trace them and find the origin of the failure.

All events registered in the system viewer have a standard ID associated with them, according to their type (Security, Audit, applications, etc.). So, whenever we see an "EventI D 41", it will mean that the famous blue screen has appeared. This impacts that some IDs will only be available if you have configured a specific functionality. For example, the event:
“Event 4662: An operation was performed on an object”.
Refers to existing objects within the Active Directory, it will only appear if we have this functionality active.
In our case, if we wanted to control the authentication, creation, deletion and modification of users, we would be monitoring the "Security Auditing" functionality. So, the events related to "Account Management" would be interesting. For example:
If you look at the Account Management events, you would be controlling the creation and deletion of new accounts, as well as knowing when an account is assigned to a security group. Events related to the Active directory allow us, for example, to see who has registered on the server with administrator permissions.
The content of an event would be as shown below:
“Event 4662: An operation was performed on an object”.
Refers to existing objects within the Active Directory, it will only appear if we have this functionality active.
Microsoft Windows Server Monitoring
Now that we know the concepts, it's time to make a monitoring plan for our server. But what events would we select? Again, the answer depends of the use and what functionality you need.In our case, if we wanted to control the authentication, creation, deletion and modification of users, we would be monitoring the "Security Auditing" functionality. So, the events related to "Account Management" would be interesting. For example:
- 4720 – A user account was created
- 4722 – A use account was enabled
- 4723 – An user attempted to change an account’s password
- 4724 – An attempt was made to reset an account’s password
- 4725 – A user account was disabled
- 4726 – A user account was deleted
- 4727 – A security-enabled global group was created
- 4728 – A member was added to a security-enabled global group
- 4729 – A member was removed from a security-enabled global group
- 4730 – A security-enabled global group was deleted
- 4731 – A security-enabled local group was created
- 4732 – A member was added to a security-enabled local group
- 4733 – A member was removed from a security-enabled local group
- 4734 – A security-enabled local group was deleted
- 4735 – A security-enabled local group was changed
- 4737 – A security-enabled global group was changed
- 4738 – A user account was changed
- 4741 – A computer account was created
- 4742 – A computer account was changed
- 4743 – A computer account was deleted
- 4754 – A security-enabled universal group was created
- 4755 – A security-enabled universal group was changed
- 4756 – A member was added to a security-enabled universal group
- 4757 – A member was removed from a security-enabled universal group
- 4758 – A security-enabled universal group was deleted
- 4726 – A user account was deleted
- 4720 – A user account was created
- 4756 – A member was added to a security-enabled universal group
- 4662 - An operation was performed on an object
- 4624 - An account was successfully logged on
- 4672 - Special privileges assigned to new logon
If you look at the Account Management events, you would be controlling the creation and deletion of new accounts, as well as knowing when an account is assigned to a security group. Events related to the Active directory allow us, for example, to see who has registered on the server with administrator permissions.
The content of an event would be as shown below:
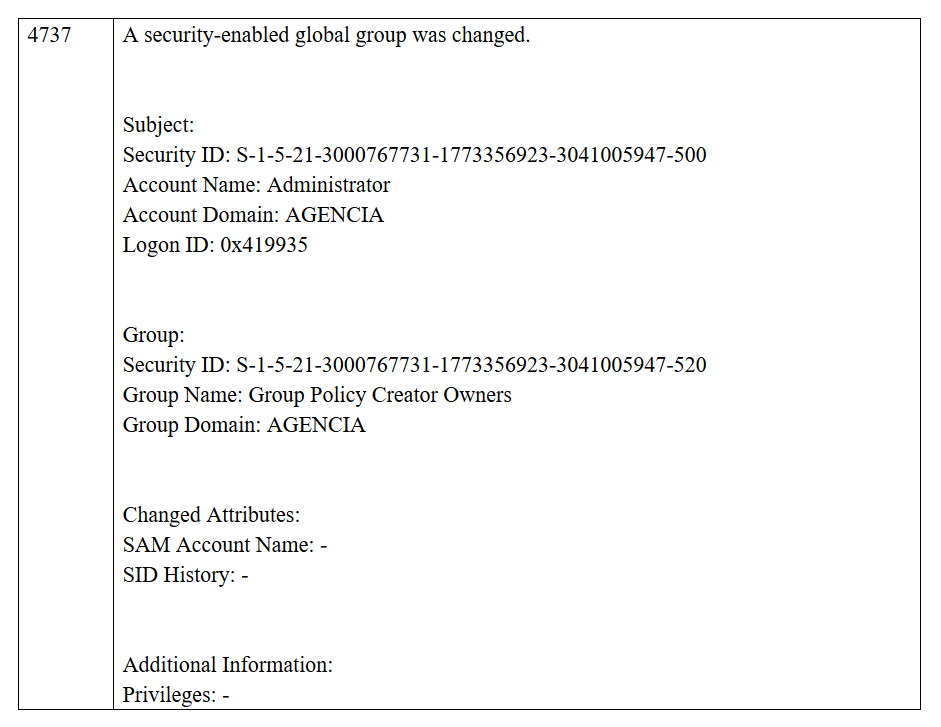
In the first column we have the code of the event and in the second a text with all the details of the event.
There are events that have a very similar or equal descriptive text. To find out which one to use, we can take a look at the category and subtype. And if we still don't have it clear. The simplest way would be to carry out a few tests that allow us to see which of them appears and if both appear, study what information it gives us.
One of the problems to face when working with Windows events is "dirt". For example, event 4662 shows any modification made to an Active Directory object; the system itself makes changes to them, which ends up generating an enormous amount of this type of events. In these cases, it is good to apply a filter to only store or study the elements with real interest.
We hope we have shed some light about event monitoring to Windows operating systems. If you have any questions or need to consult us, Muutech will be happy to assist you.
There are events that have a very similar or equal descriptive text. To find out which one to use, we can take a look at the category and subtype. And if we still don't have it clear. The simplest way would be to carry out a few tests that allow us to see which of them appears and if both appear, study what information it gives us.
One of the problems to face when working with Windows events is "dirt". For example, event 4662 shows any modification made to an Active Directory object; the system itself makes changes to them, which ends up generating an enormous amount of this type of events. In these cases, it is good to apply a filter to only store or study the elements with real interest.
We hope we have shed some light about event monitoring to Windows operating systems. If you have any questions or need to consult us, Muutech will be happy to assist you.

CEO & MANAGING DIRECTOR
Expert in IT monitoring, systems and networks.
Minerva is our enterprise-grade monitoring platform based on Zabbix and Grafana.
We help you monitor your network equipment, communications and systems!
Subscribe to our Newsletter




